A replay attack happens when a malicious actor intercepts and resends a previously transmitted message to trick the system, potentially gaining unauthorized access to sensitive information.
From hijacking online banking sessions to exploiting network vulnerabilities, replay attacks pose a serious risk to both individuals and organizations. Our blogpost will break down what a replay attack is, showcase real-world examples, and provide practical defense strategies to safeguard against them effectively in 2025.
Key Takeaways
- Replay attacks capture and resend messages to gain unauthorized access to secure systems.
- In online banking, attackers can use intercepted tokens to make repeated transactions fraudulently.
- Smart contracts on blockchain are particularly vulnerable to replay attacks without proper safeguards.
- Defenses include timestamps, encryption, and unique identifiers to secure communications.
- Techniques like one-time passwords and VPNs like TurisVPN’s encryption further help prevent replay attacks on networks.
What Is A Replay Attack?
A replay attack is when a malicious actor captures and retransmits valid data to achieve fraudulent authentication or execute unauthorized actions. Essentially, it involves intercepting and replaying communication between two parties without modifying its contents.
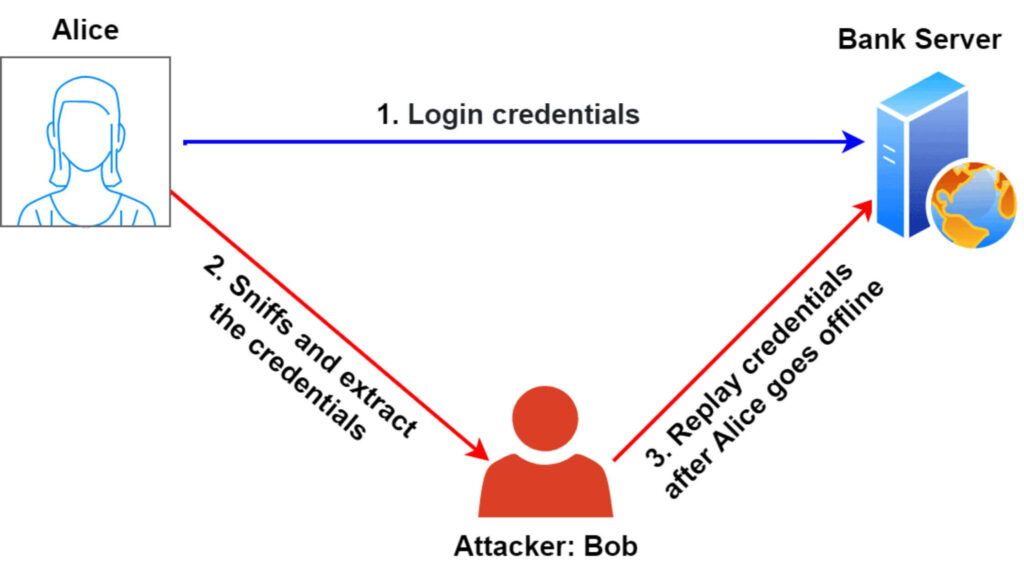
During a replay attack, an attacker eavesdrops on a secure network and intercepts sensitive data, such as login credentials or transaction requests. By resending this captured data, they can deceive the receiver into thinking it’s a valid request.
Since the hacker doesn’t need to decrypt the message, they can simply resend it, making this attack easy to execute yet dangerous.
Replay Attack on a Blockchain level
In blockchain technology, replay attack poses a risk during chain splits or in multi-chain environments. A malicious actor can replicate a valid transaction on one blockchain and broadcast it on another.
This type of attack can allow hackers to gain unauthorized access to assets by exploiting similar transaction structures across different chains.
Mitigation Strategies for Blockchain Replay Attacks:
- Chain-specific signatures: By including a unique chain identifier, such as the chainID (implemented via EIP-155), cross-chain transaction duplication is prevented.
- Nonce: Each transaction includes a unique nonce, ensuring each is a one-time action, thus blocking replays.
Replay Attack on a Smart Contract level
Within the smart contract space, replay attack exploits contract vulnerabilities within the same chain. For instance, if a smart contract lacks a unique identifier or nonce system, attackers can resend signed transactions, tricking the contract into repeated actions.
Mitigation Strategies for Smart Contract Replay Attacks:
- Nonce Tracking: Using a nonce to track each account’s transaction history helps in identifying and rejecting duplicated signatures.
- Unique Contract Identifiers: Hashing values specific to the contract, like the contract address, prevents reuse of the same signature across different contracts.
- Code Audits: Regular audits help detect replay vulnerabilities, ensuring contract logic remains secure.
How Does A Replay Attack Work?
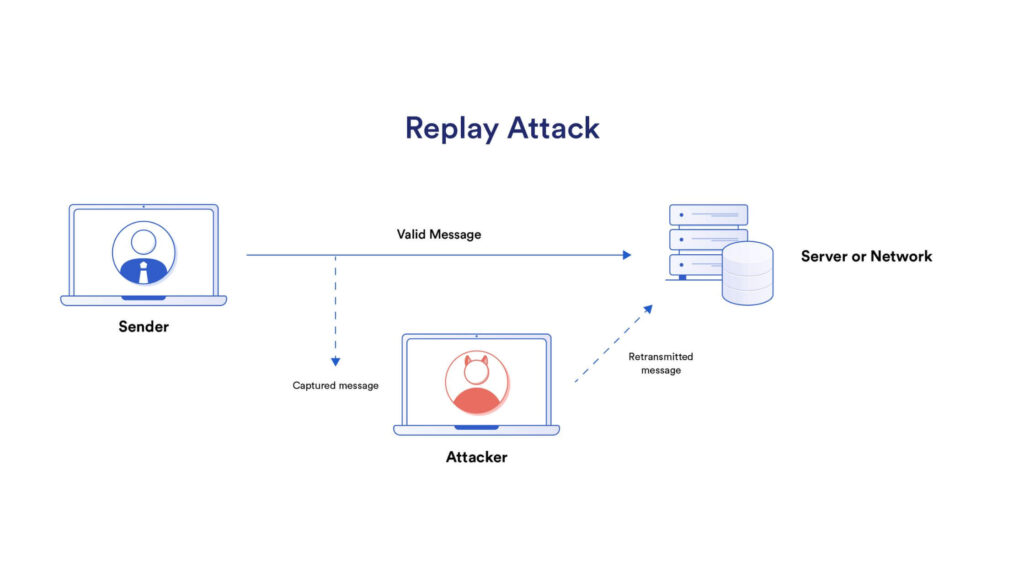
In a replay attack, a hacker intercepts a legitimate communication or transaction, saves it, and then resends it later to deceive the recipient.
Let’s look at a straightforward example:
Imagine an employee at a company sends an encrypted message to the finance department, requesting a money transfer. A hacker intercepts this request, saving the message.
Later, the hacker resends the same encrypted message to the finance team, making it appear as a legitimate request for funds.
Since the message is authentic and correctly encrypted, it seems trustworthy to the finance team, who may then proceed with the transaction—sending the funds to the attacker’s account instead of the original intended recipient.
Because the message is an exact copy, it doesn’t need modification to look valid. The danger here is that, unlike other attacks, the hacker doesn’t need to decode or alter the message; they only need to resend it at a later time to achieve their goal.
The Dangers Of Replay Attacks
Replay attacks pose serious risks, especially for organizations that rely on digital transactions and secure communications:
- Unauthorized Access: By capturing and re-sending authentication data, attackers can gain unauthorized entry to systems, leading to potential data theft and loss of sensitive information.
- Illicit Financial Transactions: In finance, replaying transaction data can authorize unauthorized transactions, resulting in serious financial losses. Attackers who capture transaction requests may replay them to initiate fraudulent payments or transfers.
- Service Disruptions: Attackers can overload or manipulate services, leading to system downtime and interruptions in critical operations. This can affect the smooth running of online services, reducing productivity and impacting revenue.

- Data Breach Potential: Even if an attacker does not decrypt the data, intercepting and replaying sensitive communications can expose vulnerabilities. In secure environments like corporate or military networks, replayed messages that appear authentic may lead to unintentional data leaks and security breaches.
- Blockchain and Smart Contract Exploits: Replay attacks can cause severe damage by exploiting user transactions on parallel chains. This enables attackers to manipulate contract states or steal assets in decentralized finance (DeFi) applications, where security is paramount for protecting user funds.
- Loss of Intellectual Property: Organizations that rely on online exchanges of proprietary data, such as design files or patents, risk having valuable intellectual property intercepted and misused through replay attacks.
Real-World Examples Of Replay Attacks
Replay attacks take various forms across different industries and security protocols. Here are some notable examples to illustrate how replay attacks occur and the impact they can have:
Online banking replay attack
In online banking, users authenticate transactions using digital tokens or signatures. In a replay attack, a hacker intercepts a valid transaction such as a fund transfer—captures the token or digital signature, and replays it to trick the system into executing unauthorized transfers.

Without mechanisms to verify the uniqueness of each transaction, the banking system may mistakenly allow repeated transfers, leading to financial losses for the account owner.
SAML replay attack
Security Assertion Markup Language (SAML) is commonly used for secure authentication. In a SAML replay attack, a cybercriminal intercepts a valid SAML assertion (the token that verifies identity during login) and replays it to access systems or applications.
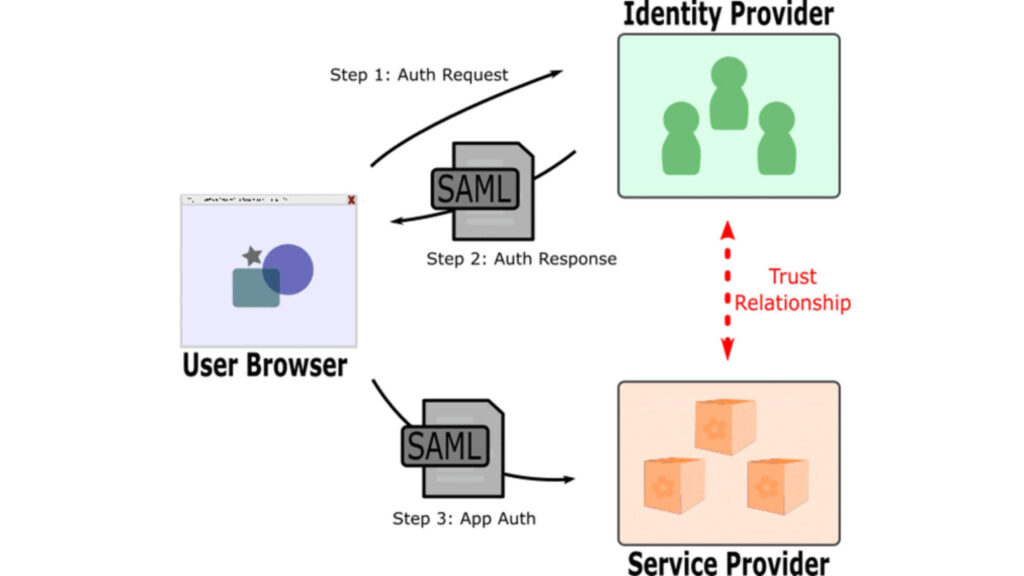
By doing so, the attacker can gain unauthorized entry to a platform, bypassing the regular login process without needing the user’s password.
Network authentication
Replay attacks within network communications involve capturing session tokens or authentication messages used to verify user access.
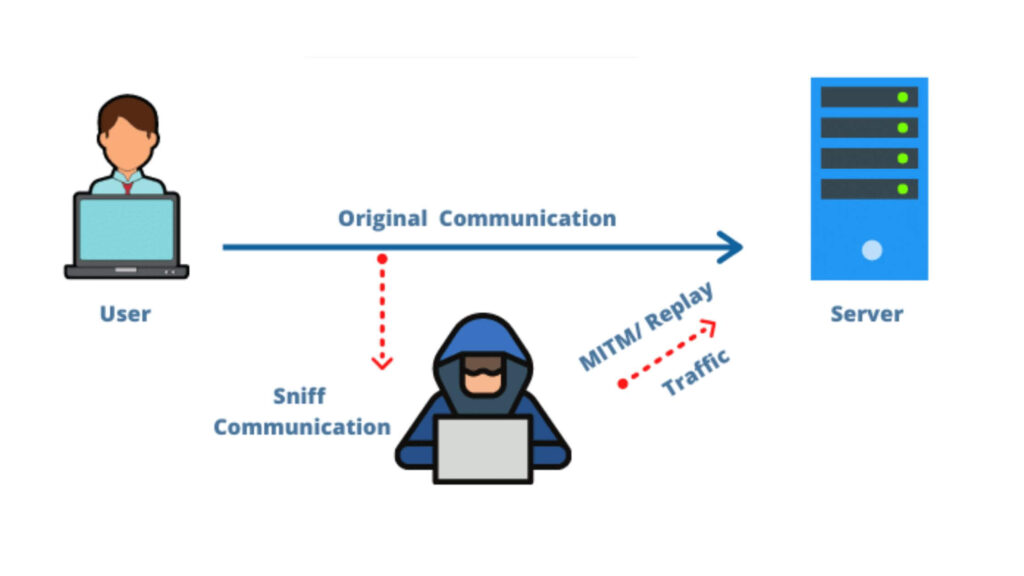
For example, a malicious actor might intercept an employee’s login credentials for a secure network. By replaying the same token later, the hacker can access the network without additional authorization, risking sensitive data and network security.
Cookie replay attack
In this type of attack, an attacker intercepts a session cookie from a user’s web session, such as while accessing a bank account or secure application. The hacker can then reuse the cookie to impersonate the user on the same website.
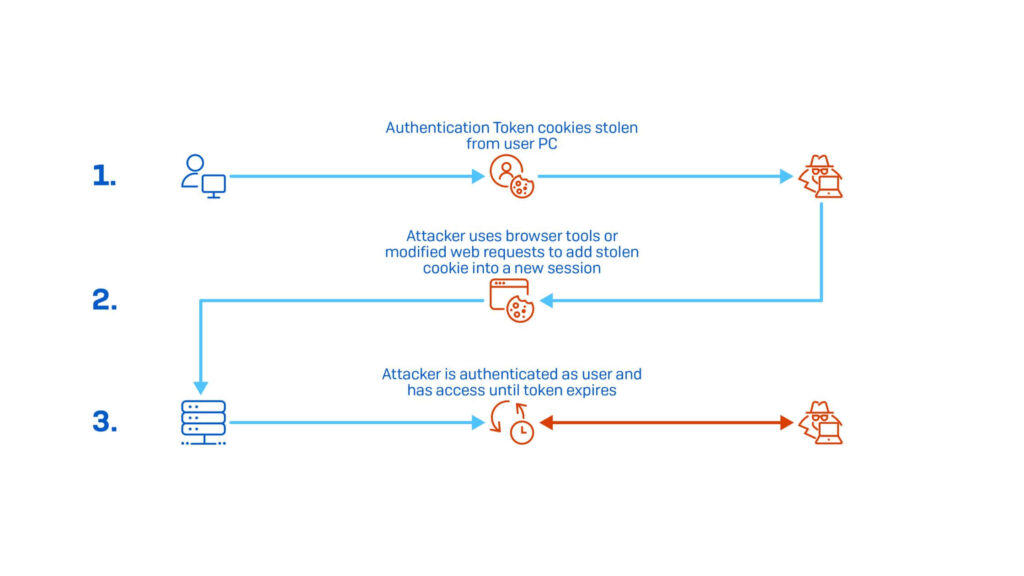
This allows unauthorized access to the user’s session, which could lead to financial theft, data exposure, or even identity theft.
HackRF replay attack
A HackRF attack involves using radio frequency (RF) interception tools to capture and replay signals. For instance, a hacker might intercept the signal from a car key fob, recording the unlock signal.
The attacker can gain access to the car without needing the actual key fob, highlighting the risk of replay attacks in physical security systems.
How To Defend Against Replay Attacks? 5 Essential Tactics
To effectively prevent replay attacks, employing specific tactics that strengthen your network and data security is critical. Here are five essential ways to protect against them:
1. Add Timestamps on all messages
Timestamps record the exact time and date of data transmission, allowing systems to identify when a message was sent and reject duplicate or delayed ones.
When each session has a unique timestamp, it becomes easier to detect and block replayed messages, as the system can recognize any discrepancies in timing. Trusted Timestamping Authorities (TSAs) can also ensure that timestamps are accurate and tamper-resistant, adding another layer of protection.
2. Encrypt your online traffic
Encrypting all data in transit makes it significantly harder for attackers to capture and manipulate your messages. TurisVPN can protect your data, making it unreadable to hackers.

TurisVPN establishes secure tunnels between your device and the server, protecting traffic on both public and private networks. This way, even if someone intercepts your session data, they can’t decrypt it or launch a replay attack.
3. Pay attention to security protocols
SSL (Secure Socket Layer) and TLS (Transport Layer Security) are encryption protocols that generate unique session keys between the origin and destination servers. Enabling these protocols on your browser ensures that every session is uniquely encrypted, deterring replay attacks.

While configuring SSL/TLS settings in browsers can enhance security, using TurisVPN with built-in WireGuard protocol can provide continuous protection across all devices and platforms.
4. Use one-time passwords (OTPs)
OTPs add an extra layer of security by providing temporary, single-use codes for authentication. Since OTPs expire quickly and cannot be reused, they prevent attackers from re-accessing a session using the same credentials.
Many platforms now incorporate OTPs for two-factor authentication (2FA), which is especially useful in high-security environments where a secure connection is essential.
5. Secure your network connections
With remote work becoming the norm, securing network connections is crucial. Many home networks lack robust security measures, and even some businesses overlook secure remote access (SRA) setups.

Using TurisVPN on all devices connected to work or sensitive networks can safeguard data transmission. TurisVPN with advanced encryption and establishes secure connections, making it difficult for attackers to intercept or replay captured data.
Bottom Line
Replay attacks pose serious risks in areas like online banking, network authentication, and blockchain. A replay attack can lead to unauthorized access, financial loss, and compromised data integrity.
Understanding how these attacks work and implementing effective defense strategies like timestamps, encryption, secure protocols, OTPs, and secure network connections can significantly strengthen your protection against them.