In 2024, Malaysia became a key target of a major cyber attack by the notorious ROOTK1T hacking group. Malaysia faces over 3,000 cyber attacks each day, making it a prime target for sophisticated cyber threats.
These attacks highlighted the severe risks posed by rootkits, a type of malware that can cause significant damage while remaining hidden from detection.
In this blog post, we’ll explain what rootkit Malaysia is, the types used in the Malaysia attack, how they were detected, and the lessons we can learn to improve cybersecurity and prevent future attacks.
Key Takeaways
- Rootkits pose a severe threat by hiding deep within systems, making them difficult to detect and remove.
- Malaysia faces over 3,000 cyber-attacks daily, with the ROOTK1T group’s attacks highlighting the need for stronger cybersecurity.
- The ROOTK1T hacker group is notorious for targeting critical sectors like finance, government, and telecommunications.
- Proactive cybersecurity measures, such as regular software updates and employee awareness, are crucial in defending against sophisticated threats.
- Using TurisVPN can add an extra layer of security, masking your IP address and encrypting online activities.
What is Rootkit?
A rootkit is a type of malicious software (malware) that allows hackers to gain unauthorized access to a computer or network without being detected.

What makes rootkits dangerous is their ability to hide deep within a system, making them difficult to detect and remove. Once a rootkit is on a device, it allows hackers to take control, bypass security, steal personal information, spread other malware, and even infect other devices.
Rootkits can provide an attacker with a backdoor into a machine. So they can change system files and processes, making them nearly invisible to most antivirus programs.
5 Types of Rootkit
Rootkits are dangerous because they can hide in different parts of a system, making them hard to find and remove. Here are five common types:
| Type of Rootkit | Target Area | Danger Level |
| Firmware | BIOS/UEFI (Low-Level Hardware Software) | Very High – Operates below the OS level. |
| Bootloader | Bootloader (Startup Process) | High – Evades detection, remains active. |
| Memory | RAM (Random Access Memory) | Moderate – Disappears after reboot. |
| Application | Legitimate Applications | High – Blends in with everyday software. |
| Kernel Mode | Core of Operating System | Very High – Controls most aspects of the system. |
Firmware
Firmware rootkits attack the low-level software that controls your computer’s hardware (BIOS or UEFI). This makes them extremely difficult to detect and remove because they operate below the OS level, essentially hiding in the “roots” of the system.
Attackers can use firmware rootkits to intercept data, disable security measures, and even spread malware to other connected devices, such as routers.
Bootloader
Bootloader rootkits infect the bootloader, which loads the operating system. These rootkits can alter how the OS is loaded, allowing attackers to take control of the system right from startup.
The special OS software loads in the memory of a computer after it starts up and is typically launched by a compact disc (CD) or digital versatile disc (DVD), hard drive, or USB stick, which tells the BIOS where the bootloader is.
This early-stage attack makes bootloader rootkits especially dangerous, as they can evade detection by most antivirus software and remain active even after system reboots.
Memory
Memory rootkits hide in the RAM (Random Access Memory) of a computer. These rootkits modify system processes in memory, making them invisible to the OS and security tools. Although they usually disappear when you restart your computer, they can still cause significant damage, such as slowing down your system or stealing sensitive data.
Application
Application rootkits replace or modify legitimate application files with malicious versions. For instance, they might infect common programs like Notepad or Paint.
When a user runs these infected applications, the rootkit gives hackers access to the system, all while the program appears to function normally. This makes application rootkits hard to detect because they blend in with everyday software, often going unnoticed by both users and antivirus programs.
Kernel mode
Kernel mode rootkits are the most dangerous because they target the core of the operating system, giving hackers complete control over the system. They can manipulate anything from file systems to network connections, making them extremely hard to detect and remove. Once a kernel rootkit is in place, it can control almost every aspect of the infected device.
How to detect infection from Rootkit?
Rootkits are tricky because they hide deep in your system, making them hard to find.
However, there are some signs that might hint at a rootkit infection:
- Frequent crashes or blue screens: If your computer keeps crashing or shows the “blue screen of death” often, a rootkit could be messing with your system’s core processes.
- Slow performance: When you see your computer suddenly slows down, takes forever to start, or freezes a lot. It may be because these hidden programs use up system resources, which can make your device sluggish.
- Weird browser behavior: You might notice unexpected redirects, new bookmarks you didn’t add, or trouble accessing certain websites. This strange behavior could be a sign that a rootkit is at work.
- Unusual system change: Your computer’s settings are changing without your input, like a different screensaver or the wrong time and date. These changes happen because rootkits often tweak settings to stay hidden.
- Unusual network activity: Notice your internet is slow or see lots of unexpected network activity? Rootkits might be using your connection to communicate with a hacker’s server.
- Disabled security software: If your antivirus suddenly stops working or you can’t update it, a rootkit might be trying to prevent itself from being found.
- Hidden files or processes: If you find files you didn’t create, or your antivirus alerts you to something it can’t fix, a rootkit could be the cause.
Who is ROOTK1T Malaysia Hacker Group?
ROOTK1T is a notorious hacker group known for carrying out sophisticated cyber-attacks across various sectors such as finance, government, and telecommunications.
They’ve claimed responsibility for attacks on big companies like L’Oreal, Qatar Airways, and Sodexo, as well as the Lebanese Government.
On January 26th, ROOTK1T announced on their Telegram channel that they would be launching a cyber-attack against key infrastructure in Malaysia. This campaign was part of their “retaliation team” efforts, in response to cyber-attacks linked to conflicts in the Middle East.
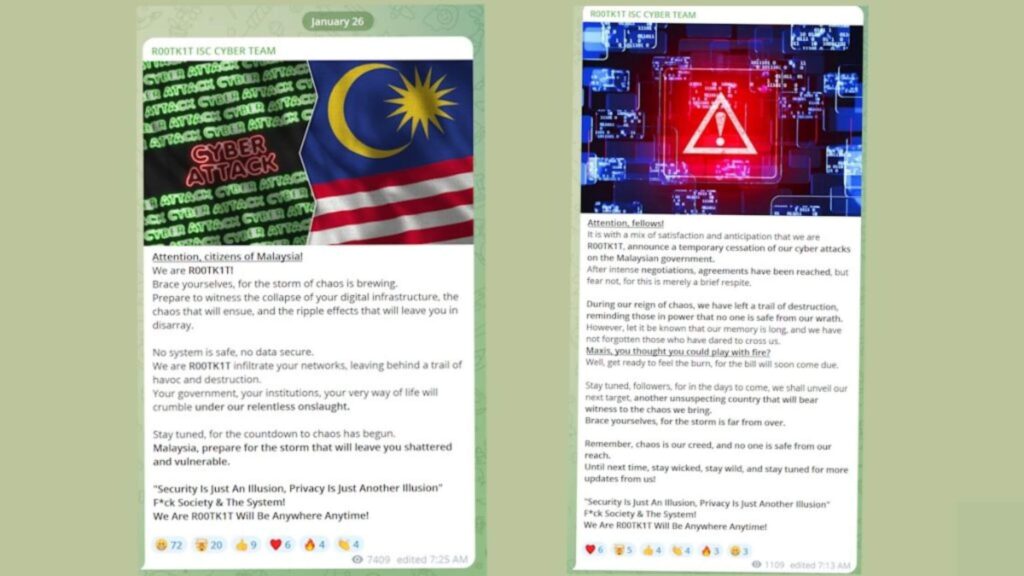
The group’s activities have raised alarm, particularly because Malaysia experiences over 3,000 cyber-attacks daily. ROOTK1T’s attacks have added to the already high pressure on Malaysian cybersecurity defenses, highlighting the need for enhanced security measures and awareness about such threats
Impact of ROOTK1T in Malaysia
The ROOTK1T cyber attacks have had a serious and far-reaching impact on Malaysia. In January 2024, the group launched a series of attacks that targeted important sectors like telecommunications, education, and IT services.
These attacks led to major breaches, including website defacement, stolen data, and service disruptions.

Aminia was one of the first companies to be affected, confirming a breach, although they stated that no sensitive data was leaked. YouTutor, another target, had its website altered and user data exposed. Maxis, a leading telecom company, faced ongoing threats and alleged breaches, which led to increased concern over its security measures.
These attacks have shown how vulnerable Malaysia’s infrastructure is to advanced cyber threats. As a result, both companies and the government are now focusing on improving their cybersecurity.
The National Cyber Coordination and Command Centre (NC4) has issued warnings to all organizations, urging them to strengthen their defenses to prevent further damage. The continuing threats from ROOTK1T in Malaysia have not only disrupted operations but have also highlighted the need for stronger cybersecurity strategies across the country.
What To Learn From ROOTK1T Malaysia Case Study?
The ROOTK1T attacks on Malaysia provide several critical lessons in cybersecurity for individuals and organizations alike:
- Proactive security measures: Implementing proactive security measures includes using firewalls, endpoint protection, and zero-trust architecture to prevent unauthorized access and reduce the chances of cyber-attacks like those from ROOTK1T.
- Regular software updates: Keeping your software, systems, and applications up-to-date is one of the best defenses against rootkits and other malware. Regular updates ensure that vulnerabilities are patched before hackers can exploit them. .
- Employee awareness: : Many cyber breaches occur due to human error. Regular cyber awareness training for employees helps them recognize phishing attempts and other threats, which significantly lowers the risk of an attack.
- Practice Basic Cyber Hygiene: For individuals, it’s crucial to follow basic cybersecurity practices like avoiding phishing emails, keeping systems updated, backing up data regularly, and being cautious with downloads and attachments. These simple steps can help prevent rootkit infections.
- Use a VPN for Enhanced Security: TurisVPN provides an additional layer of protection by masking your IP address and encrypting your online activities. This makes it harder for hackers to track or target your browsing sessions, offering an extra level of privacy and security.

Bottom Line
The ROOTK1T Malaysia cyber attacks show how dangerous it can be online. They can hide deep in systems, causing major problems while staying undetected.
To stay safe, it’s important to keep your software updated, be aware of threats like rootkits, and use TurisVPN to protect your online activity. With cyber-attacks increasing, especially in Malaysia, focusing on cybersecurity has never been more crucial.