Cyberattacks are getting sneakier every day, Pegasus spyware stands out as one of the most alarming threats. This isn’t your average virus, this advanced spyware can break into your phone without you even clicking a link. Losing all control of your phone, with every message, photo, and personal detail exposed to dangerous hackers. The consequences can be devastating, all data just waiting to be exploited.
In this article, you’ll learn how to recognize and avoid the Pegasus spyware scam. We’ll break down the warning signs behind this suspicious software and give you clear, actionable steps to protect your data. You’ll get all the information from identifying suspicious behavior on your devices to understanding how these scams operate.

Key Takeaways:
- Pegasus Spyware is Real: Pegasus is an advanced spyware used by governments for surveillance. Pegasus spyware is capable of infecting devices through zero-click methods
- Beware of Phishing Scams: Scammers frequently exploit high-profile cyber threats like Pegasus spyware to scare victims into paying ransoms.
- Use a VPN for Enhanced Security: Protect your online activity by encrypting your traffic and hiding your IP address, reducing the risk of falling victim to phishing scams.
What Is The Pegasus Spyware Scam? What Does It Include?
The Pegasus spyware is one of the most advanced and invasive forms of spyware known today, affecting both Android and iOS devices. Developed by the Israeli company NSO Group, it was initially designed to assist governments in tracking terrorists and criminals.
However, it has been at the center of controversy due to its misuse by some governments and organizations to target high-profile individuals like journalists, activists, and politicians. The fact that it can be installed covertly without requiring the victim to take any action is a real nightmare.

Cybercriminals have also capitalized on the widespread fear of Pegasus by launching Pegasus sextortion scams. In this scam, victims receive emails claiming that their device has been hacked using Pegasus spyware. The attackers then threaten to release sensitive personal information unless a ransom is paid, typically in Bitcoin.
How Does Pegasus Scam Work?
Pegasus uses zero-click exploits, which means that it can infect your device without you needing to click on anything. Unlike traditional malware that requires a click on a malicious link or an app download, Pegasus can breach your phone just through a missed call or a simple message. Once inside your device, it gains full access to your calls, text messages, photos, videos, emails, and even your microphone and camera
For example, reports from Amnesty International revealed that over 50,000 phone numbers had been targeted globally using Pegasus spyware, including politicians, human rights activists, and even heads of state like French President Emmanuel Macron. A staggering 45 countries have been identified as potential regions where Pegasus has been used.
Pegasus is able to perform all of this without the target having to do anything. The infection method is extremely covert, frequently leaving no evidence of the spyware’s presence on the device to notify the user.

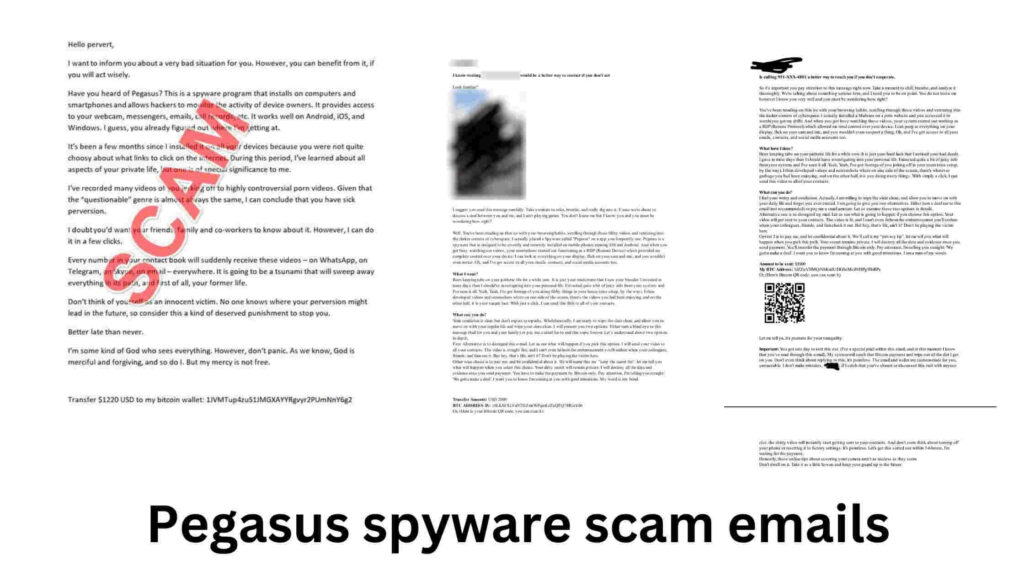
Real Examples Of Pegasus Spyware Scam Emails
These scams prey on users’ anxiety by claiming that their devices have been infected with Pegasus spyware and demand payment to prevent exposure of sensitive data. In this article, we’ll explore real examples of Pegasus spyware scam emails:
1. The Sextortion Email Scam: Claiming to Record You
One of the most common types of Pegasus scam emails is the sextortion scam. In this type of scam, victims receive an email claiming that the sender has installed Pegasus spyware on their phone or computer. The email often asserts that the spyware has been used to secretly record the victim through their device’s camera while they engaged in embarrassing or compromising behavior.
Example:
A typical email might look like this:
“I’ve installed Pegasus spyware on your phone, and I have access to your camera and microphone. I recorded you while you were watching inappropriate content. I have videos and will send them to your contacts unless you pay me $1500 in Bitcoin within 48 hours.”
The attacker may even include personal details like the victim’s home address (often found through public sources like Google Maps) to make the email appear more credible. The scammer’s goal is to create fear and urgency, convincing the recipient to pay quickly without verifying the claims
Reality:
In most cases, no spyware has been installed, and no recordings exist. The scammers rely on fear to manipulate the victim. Ignore the email and run a malware scan on your device just to be safe. Never respond or pay the ransom, as this will encourage further extortion attempts.
2. The “We Have Everything” Phishing Email
Another scam involves emails that claim the sender has gained full control over the victim’s device using Pegasus spyware. These emails typically declare that everything—emails, photos, contacts—has been stolen, and a ransom is demanded to avoid the release of the data.
Example:
An email might say:
“Your device was hacked using Pegasus spyware. We have all your messages, photos, and contacts. Pay $2000 in Bitcoin, or we’ll release this information publicly. Don’t try contacting the authorities, or we’ll release your data immediately.”
The scammers often include snippets of the victim’s email address or public social media details to make the claim seem legitimate. However, these details are easily accessible through data breaches and public records, making them unreliable indicators of an actual breach. Scammers will often use a technique known as email spoofing to make it seem like the email came from your own account or a trusted contact.
Reality:
These phishing emails usually contain no real evidence of a hack. Scammers rely on public information to scare the recipient into compliance. In reality, Pegasus infections are rare, and high-profile individuals, not regular users, are the usual targets
3. Changing Your Password email
In another variation of the Pegasus spyware scam, scammers send emails claiming that Pegasus has gained access to all of your accounts, including email, social media, and banking. One victim on a Reddit thread shared that the scam email demanded a Bitcoin payment and included screenshots of their email account’s password page to convince them of a hack.
Example:
“Your accounts have been compromised by Pegasus spyware. We have your email and social media passwords, and we will start changing your passwords unless you pay us $2,000 in Bitcoin.”
The email may even include a password the user has previously used, sourced from older data breaches, to add legitimacy to the threat.
Reality:
In most cases, the attacker doesn’t have control of your accounts, but they may have obtained old passwords from a previous data leak. These passwords are often no longer valid.
Are You Hacked By Pegasus Scam?
Yes, Pegasus spyware can indeed hack both mobile phones and potentially other devices like PCs, although it primarily targets smartphones.
Pegasus is designed to avoid detection and operates covertly once it infects a device. However, there are specific signs and tools that can help identify whether your device has been compromised.

Key Signs of Pegasus Infection
- Unusual Battery Drain: Pegasus spyware continuously runs in the background, which can lead to increased battery consumption. If your phone’s battery is draining much faster than usual without any change in usage habits, it could indicate spyware activity.
- Unusual Behavior: If your device starts behaving erratically—apps opening or closing on their own, unexplained messages being sent, or unexpected reboots—this could be a sign of malware, including Pegasus spyware.
- Encrypted Messages: Pegasus often exploits messaging apps like WhatsApp to deliver the infection. If you see strange messages or encrypted communication from unknown contacts, it may be a sign that your device was targeted by a zero-click exploit.
How To Protect Yourself Against Pegasus Scam?
Pegasus spyware scams leverage fear and deception to trick individuals into paying ransoms. These scams prey on our concerns about privacy and cybersecurity.
- Ignore Suspicious Emails: Do not respond to ransom demands or threats. Scammers rely on fear to get victims to comply quickly.
- Run Security Scans: Use trusted antivirus or anti-malware software to scan your device if you suspect a breach.
- Update Passwords: If a scammer claims to have access to your accounts, update your passwords immediately. Use strong, unique passwords for each account, and enable two-factor authentication whenever possible.
- Report Phishing Attempts: Most email providers have an option to report phishing emails. This helps block future scams.
- Stay Informed: Keep up with the latest phishing scams, like the Pegasus spyware scam, so you can recognize them and avoid falling victim.
What Are Other Phishing Scams Like Pegasus To Stay Aware About?
Let’s explore two other significant phishing scams that are making the rounds, and how to stay safe from them.
1. OfferUp Scams
OfferUp is a popular marketplace for buying and selling items locally. However, like any online platform, it’s not immune to scammers. A common phishing scam on OfferUp involves fraudulent buyers or sellers.
Scammers pose as interested parties but use fake payment methods or manipulate victims into sharing sensitive information like bank account details or credit card numbers. They often lure victims with low prices or pressure them to act quickly, exploiting the buyer’s eagerness to close a good deal.

2. Geek Squad Scams
The Geek Squad scam is another phishing scam to watch out for. In this scheme, scammers pretend to be representatives of Best Buy’s Geek Squad tech support service, sending fake invoices or alerts claiming you’ve been charged for a subscription service.
They encourage the victim to call a provided number to “cancel” the charge, where the scammer then tries to gather personal information or convince the target to install remote-access software, gaining control of their device. These types of scams can lead to severe financial losses or even identity theft.
Stay Safe Online With Turisvpn
While threats like Pegasus spyware grab headlines, other phishing scams such as OfferUp scams and Geek Squad scams also pose significant risks. Fortunately, using a VPN like TurisVPN can add an extra layer of security, helping you navigate the internet safely and privately.

When you’re targeted by these scams, one of the primary threats is that your online activity could be monitored, or your personal data could be intercepted. This is where a VPN comes in handy.
TurisVPN’s WireGuard VPN offers an excellent balance between security and performance, it can shield your IP address and encrypt your internet traffic. Making it far more difficult for scammers to access your data, even if they attempt to track your online behavior.
Bottom Line
The Pegasus spyware scam is one of the most alarming cyber threats, exploiting fear to steal money and personal data. However, understanding how it works and staying informed about phishing tactics can protect you from falling victim.
The key to staying safe online lies in carefulness and security measures. Using a VPN like TurisVPN adds a critical layer of protection, shielding your online activity and keeping your data secure from scammers.
FAQs
Q1. Is The Pegasus Spyware Scam A Hoax?
The Pegasus spyware itself is real, developed by the NSO Group and used by governments for surveillance. However, many phishing scams pretend to use Pegasus to scare people into paying ransoms, and these emails are hoaxes.
Q2. Did India Buy Pegasus Spyware In 2017?
There are allegations that India purchased Pegasus spyware in 2017, but the Indian government has not confirmed or denied it. Investigations have suggested its use for surveillance, sparking political controversy.
Q3. How To Know Your Device Infected?
Signs include unusual battery drain, increased data usage, and slowed performance. Once you notice one of those signs, install tools or apps to detect malware and hack.